The short answer is: probably not, but theoretically it’s possible.
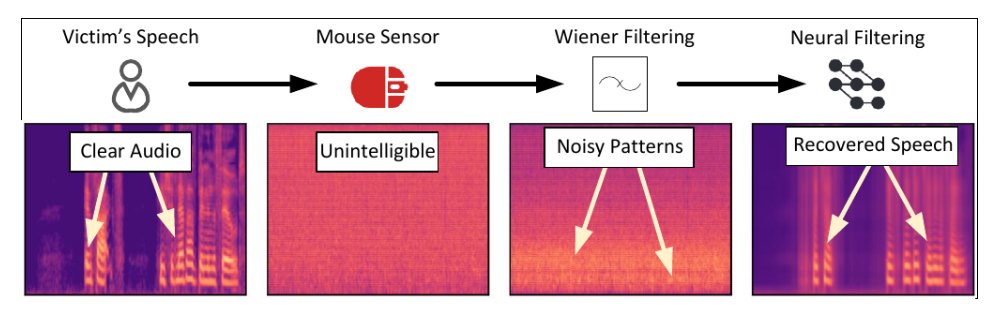
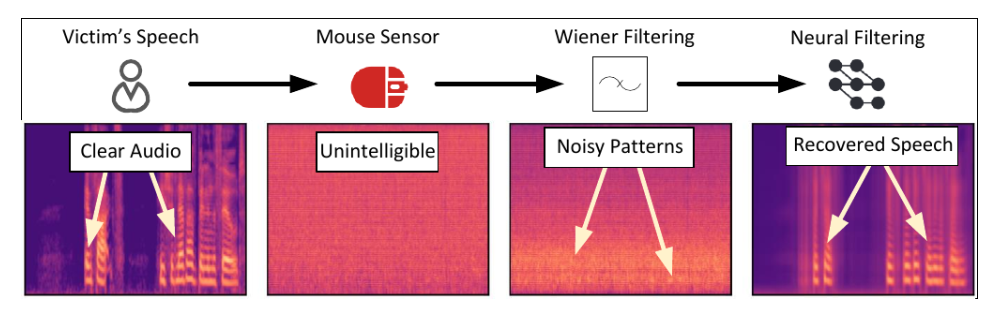
Researchers at the University of California found a method they called Mic-E-Mouse, which turns your computer mouse into a spy that can listen in on your conversations.
The method uses high-performance optical sensors in optical mice, combined with artificial intelligence, to filter out background noise and:
“achieve intelligible reconstruction of user speech.”
These sensors are highly sensitive (sometimes up to 20,000 dots per inch) and can detect the tiniest vibrations. And the attack doesn’t require expensive gear—the researchers used a $35 mouse to test their method and achieved 61% accuracy.
This is a classic side-channel attack—a way of stealing secrets not by breaking into software, but by observing physical clues that devices give off during normal use.
For example, let’s suppose you wanted to figure out someone’s bank password. A direct attack might involve trying to guess or steal the password. A side-channel attack, on the other hand, would be more like watching how they type, listening to the rhythm of their keyboard, or even detecting their body language as they log in.
What’s concerning about side-channel attacks is that they often don’t leave obvious clues.
Because the computer keeps working normally, there are usually no traces in logs, security alerts, or signs that anything’s wrong. Traditional defenses like antivirus software or firewalls can’t always detect them because these attacks rely on physical behavior—how a computer uses power, emits signals, or makes noise—which can’t easily be isolated or blocked without changing how the hardware itself works.
But it is possible to counter such an attack, since Mic-E-Mouse requires the target computer to run special software that security tools may detect as malicious. At some point, the software must send the collected data to the attacker, increasing the chance it will be intercepted. To avoid detection, attackers are unlikely to reconstruct speech on the victim’s computer; instead they may transfer the raw mouse-movement files directly to a computer or server they control somewhere on the internet.
For most users, this vulnerability isn’t cause for alarm. It’s noteworthy mainly because it transforms a trusted peripheral into a potential listening device without any visible signs or behavioral changes. But as high-DPI mice are now common in offices and gaming setups, this attack vector could be exploited by cybercriminals or spies to capture personal information, trade secrets, or private conversations. So, if you’re working in environments such as corporate offices, government sites, or home offices used for confidential tasks, the risk is higher.
What can I do about Mic-E-Mouse?
The researchers have notified 26 affected mouse manufacturers, which are now developing fixes to protect sensor data.
Until then, if you’re worried about this type of attack being deployed against you:
- Use a mouse mat or desk cover to reduce the mouse’s ability to collect data via vibrations.
- Work in a noisier environment (we recommend music).
- Keep your mouse firmware and drivers up to date—manufacturers may release security patches.
- Use up-to-date real-time anti-malware, preferably with a web protection component to block malicious software and outgoing traffic to known malicious servers.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.