The online world is changing fast. Every week, new scams, hacks, and tricks show how easy it’s become to turn everyday technology into a weapon. Tools made to help us work, connect, and stay safe are now being used to steal, spy, and deceive.
Hackers don’t always break systems anymore — they use them. They hide inside trusted apps, copy real websites, and trick people into giving up control
Author: ravencybersec_r7bgbo
-

ThreatsDay Bulletin: $15B Crypto Bust, Satellite Spying, Billion-Dollar Smishing, Android RATs & More
-

CISA Flags Adobe AEM Flaw with Perfect 10.0 Score — Already Under Active Attack
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a critical security flaw impacting Adobe Experience Manager to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The vulnerability in question is CVE-2025-54253 (CVSS score: 10.0), a maximum-severity misconfiguration bug that could result in arbitrary code execution. -
Open PLC and Planet vulnerabilities
Cisco Talos’ Vulnerability Discovery & Research team recently disclosed one vulnerability in the OpenPLC logic controller and four vulnerabilities in the Planet WGR-500 router.
For Snort coverage that can detect the exploitation of these vulnerabilities, download the latest rule sets from Snort.org, and our latest Vulnerability Advisories are always posted on Talos Intelligence’s website.
OpenPLC denial-of-service vulnerability
Discovered by a member of Cisco Talos.
OpenPLC is an open-source programmable logic controller intended to provide a low cost industrial solution for automation and research.
Talos researchers found TALOS-2025-2223 (CVE-2025-53476), a denial-of-service vulnerability in the ModbusTCP server functionality of OpenPLC_v3. A specially crafted series of network connections can prevent the server from processing subsequent Modbus requests. An attacker can open a series of TCP connections to trigger this vulnerability.
Planet WGR-500 stack-based buffer overflow, OS command injection, format string vulnerabilities
Discovered by Francesco Benvenuto of Cisco Talos.
The Planet Networking & Communication WGR-500 is an industrial router designed for Internet of Things (IoT) networks, particularly industrial networks such as transportation, government buildings, and other public areas. Talos found four vulnerabilities in the router software.
TALOS-2025-2226 (CVE-2025-54399-CVE-2025-54402) includes multiple stack-based buffer overflow vulnerabilities in the formPingCmd functionality. A specially crafted series of HTTP requests can lead to stack-based buffer overflow.
TALOS-2025-2227 (CVE-2025-54403-CVE-2025-54404) includes multiple OS command injection vulnerabilities in the swctrl functionality. A specially crafted network request can lead to arbitrary command execution.
TALOS-2025-2228 (CVE-2025-48826) is a format string vulnerability in the formPingCmd functionality of Planet WGR-500. A specially crafted series of HTTP requests can lead to memory corruption.
TALOS-2025-2229 (CVE-2025-54405-CVE-2025-54406) includes multiple OS command injection vulnerabilities in the formPingCmd functionality. A specially crafted series of HTTP requests can lead to arbitrary command execution.
-
Chinese Threat Group ‘Jewelbug’ Quietly Infiltrated Russian IT Network for Months
A threat actor with ties to China has been attributed to a five-month-long intrusion targeting a Russian IT service provider, marking the hacking group’s expansion to the country beyond Southeast Asia and South America.
The activity, which took place from January to May 2025, has been attributed by Broadcom-owned Symantec to a threat actor it tracks as Jewelbug, which it said overlaps with -
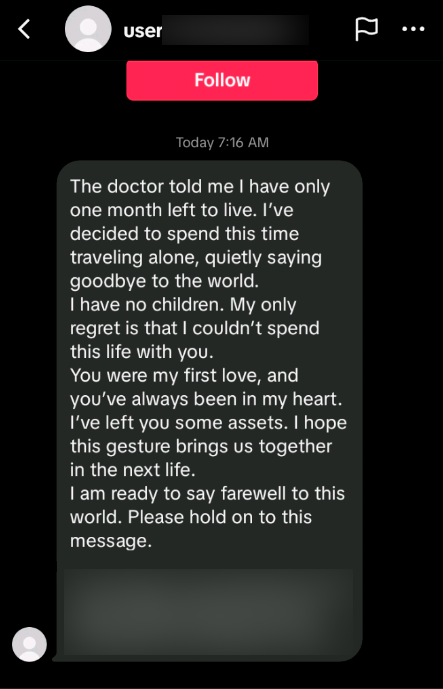
TikTok scam sells you access to your own fake money
This scam starts in your TikTok DMs. A brand-new account drops a melodramatic message—terminal illness, last goodbye, “I left you some assets.” At the bottom: a ready-made username and password for a crypto site you’ve never used. It’s designed to feel urgent and personal so you tap before you think. The whole funnel is built for phones: big tap targets, short copy, sticky chat bubbles—perfect for someone arriving straight from TikTok.
I walked through the flow so you don’t have to.
What the site shows vs. what actually exists
The illusion:
The moment you log in with the credentials from that TikTok DM, a glossy, mobile-friendly dashboard flashes a huge balance. There’s motion (numbers “update”), a believable “history,” and a big Withdraw button right where your thumb expects it. On a small screen, it looks like a real account with real money.The trap:
When you try to send that balance to your own wallet, the site asks for a withdrawal key belonging to the original account holder—the one from the DM. You don’t have that key, and support won’t give it to you. External withdrawals are a dead end by design.The detour they push you to take:
Support suggests using Internal Transfer instead. Conveniently, they also offer to help you create a new user “in seconds,” and this new account will have its own key (because you created it). That makes it feel like you’re finally doing something legitimate: “I’ll just transfer the funds to my new account and then withdraw.”The paywall you only meet once you’re invested:
Internal transfers only work on “VIP” accounts. To upgrade to VIP, you must pay for a membership. Many victims pay here, assuming it’s a one-time hurdle before they can finally withdraw.Why nothing real ever leaves the site:
After you upgrade and attempt the internal transfer, the site can:- demand another fee (a “limit lift,” “tax,” or “security key”),
- fail silently and push you to support, or
- “complete” the transfer inside the fake ledger while still blocking any external withdrawal.
Victims end up paying for the privilege of moving fake numbers between fake accounts—then paying again to “unlock” a withdrawal that never happens.
The scam in a nutshell
This scam is built for volume. DMs and comments via a huge platform like TikTok seed the same gift-inheritance story to thousands of people at once.
Two things do the heavy lifting:
- Shock value: That huge, unexpected number on the dashboard delivers a little jolt of surprise mixed with excitement, which lowers skepticism and pushes you into fast, emotional decision-making.
- Foot-in-the-door: Small steps (log in > try withdraw > hit a roadblock > “just upgrade to VIP”) nudge you toward paying a fee that now feels reasonable.
With borrowed authenticity from a big on-screen balance, the scammers sell you VIP access to move that fake balance around internally while keeping you forever one step away from a real, on-chain withdrawal.
Why do people keep paying up?
- The balance looks real, so every new hurdle feels like bureaucracy, not fraud.
- Paying once creates sunk cost: “I’ve already invested—one more step and I’m done.”
- Internal movements inside their dashboard mimic progress, even though no on-chain transfer ever occurs.
- A mobile flow encourages momentum—it’s always “one more tap” to finish.
Any system that makes you pay to receive money that allegedly already belongs to you is likely to be a scam.
The part most people miss is that you’re also handing over personal data. Even if you never send crypto, the site and the chat funnel collect a surprising amount of information, including your name, email, and phone number.
That data is valuable on its own and makes follow-up scams easier. Phishing that references the earlier “account,” extortion threats, fake “refund” offers that ask for remote access, SIM-swap attempts tied to your number, or simple resale of your details to other crews—and sadly, getting hooked once increases the odds you’ll be targeted again.
How to recognize this family of scams
- You’re asked to log into a site with credentials someone else gave you.
- A big balance appears instantly, but external withdrawals require a mystery key or never complete.
- You’re told internal transfers are possible only after buying VIP or a membership.
- The support bubble is quick to reply about upgrades and silent about on-chain withdrawals.
- Any “proof” of funds exists only inside their dashboard—no public ledger, no small test withdrawal.
How to stay safe
There are safer ways to test claims (without losing money):
- Never pay to “unlock” money. If funds are yours, you don’t buy permission to move them.
- Ask for on-chain proof. Real balances live on a public ledger. If they can’t show it, it doesn’t exist.
- Attempt a tiny withdrawal first to a wallet you control—on legitimate platforms, that’s routine after verifying your identity (know you customer, or KYC) and enabling two-factor authentication (2FA).
- Search the flow, not just the brand. Scam kits change names and domains, but the “VIP to withdraw” mechanic stays the same.
What to do if you already engaged:
- Stop sending funds. The next fee is not the last fee.
- Lock down accounts: change passwords, enable 2FA, reset app passwords, and review recovery phone/email.
- Reduce future targeting: consider a new email/number for financial accounts and remove your number from public profiles.
- Document everything (screenshots, timestamps, any wallet addresses or TXIDs if you paid).
- Report the TikTok account and the website, and file with your local cybercrime or consumer-protection channel.
- Tell someone close to you. Shame keeps people quiet; silence helps the scammers.
If a platform says there’s a pile of crypto waiting for you but you must buy VIP to touch it, you’re not withdrawing funds; you’re buying a story. TikTok brings you in on your phone; the mobile UI keeps you tapping. Close the tab, report the DM, and remember: dashboards can be faked, public ledgers can’t.
We don’t just report on scams—we help detect them
Cybersecurity risks should never spread beyond a headline. If something looks dodgy to you, check if it’s a scam using Malwarebytes Scam Guard, a feature of our mobile protection products. Submit a screenshot, paste suspicious content, or share a text or phone number, and we’ll tell you if it’s a scam or legit. Download Malwarebytes Mobile Security for iOS or Android and try it today!
-
F5 Breach Exposes BIG-IP Source Code — Nation-State Hackers Behind Massive Intrusion
U.S. cybersecurity company F5 on Wednesday disclosed that unidentified threat actors broke into its systems and stole files containing some of BIG-IP’s source code and information related to undisclosed vulnerabilities in the product.
It attributed the activity to a “highly sophisticated nation-state threat actor,” adding the adversary maintained long-term, persistent access to its network. The -
Scammers are still sending us their fake Robinhood security alerts
A short while ago, our friends at Malwaretips wrote about a text scam impersonating Robinhood, a popular US-based investment app that lets people trade stocks and cryptocurrencies. The scam warns users about supposed “suspicious activity” on their accounts.
As if to demonstrate that this phishing campaign is still very much alive, one of our employees received one of those texts.
“Alert!
Robinhood Securities Risk Warning:
Our automated security check system has detected anomalies in your account, indicating a potential theft. A dedicated security check link is required for review. Please click the link below to log in to your account and complete the security check.
Immediate Action: https://www-robinhood.cweegpsnko[.]net/Verify
(If the link isn’t clickable, reply Y and reopen this message to click the link, or copy it into your browser.)
Robinhood Securities Official Security Team”
As usual, we see some red flags:
- Foreign number: The country code +243 belongs to the Democratic Republic of the Congo, not the US, where the real Robinhood is based.
- Urgency: The phrase “Immediate Action” is designed to pressure you.
- Fake domain: The URL that tries to look like the legitimate robinhood.com website.
- Reply: The instructions to reply “Y” if a link isn’t clickable are a common phishing tactic.
But if the target follows the instructions to visit the link, they would find a reasonably convincing copy of Robinhood’s login page. It wouldn’t be automatically localized like the real one, but nobody in the US would know the difference. Logging in there hands the scammers your Robinhood login credentials and allows them to clean out your account.
According to Malwaretips, some of the fake websites even redirected you to the legitimate site after showing the “verification complete” message.
They also warned that some scammers will try to harvest additional personal data from the account, including:
- Tax documents
- Full name
- Social Security Number (if on file)
- Bank account information
How to stay safe
What to do if you receive texts like these
The best tip to stay safe is to make sure you’re aware of the latest scam tactics. Since you’re reading our blog, you’re off to a good start.
- Never reply to or follow links in unsolicited tax refund texts, calls, or emails, even if they look urgent.
- Never share your Social Security number or banking details with anyone claiming to process your tax refund.
- Go direct. If in doubt, contact the company through official channels.
- Use an up-to-date real-time anti-malware solution, preferably with a web protection component.
Pro tip: Did you know that you can submit suspicious messages like these to Malwarebytes Scam Guard, which instantly flags known scams?
What to do if you clicked the phishing link
- Change your Robinhood password
- Enable two-factor authentication (2FA) if you haven’t already.
- Contact Robinhood support through the official support channels.
- Report the scam to Robinhood and other relevant authorities.
Indicators of compromise (IOCs)
www-robinhood.cweegpsnko[.]net
www-robinhood.fflroyalty[.]com
robinhood-securelogin[.]com
robinhood-verification[.]net
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
-
Over 100 VS Code Extensions Exposed Developers to Hidden Supply Chain Risks
New research has uncovered that publishers of over 100 Visual Studio Code (VS Code) extensions leaked access tokens that could be exploited by bad actors to update the extensions, posing a critical software supply chain risk.
“A leaked VSCode Marketplace or Open VSX PAT [personal access token] allows an attacker to directly distribute a malicious extension update across the entire install base,” -
Bypassing WAFs Using Oversized Requests
Many web application firewalls (WAFs) can be bypassed by simply sending large amounts of extra data in the request body along with your payload. Most WAFs will only process requests up to a certain size limit. How the WAF is configured to handle these large requests determines exploitability, but some common WAFs will allow it by default.
The post Bypassing WAFs Using Oversized Requests appeared first on Black Hills Information Security, Inc..
-
Satellites leak voice calls, text messages and more
Scientists from several US universities intercepted unencrypted broadcast through geostationary satellites using only off-the-shelf equipment on a university rooftop.
Geostationary satellites move at the same speed as the Earth’s rotation so it seems as though they are always above the same exact location. To maintain this position, they orbit at an altitude of roughly 22,000 miles (36,000 kilometers).
This makes them ideal for relaying phone calls, text messages, and internet data. Since these satellites can cover vast areas—including remote and hard-to-reach areas—they provide reliable connectivity for everything from rural cell towers to airplanes and ships, even where cables don’t reach.
That same stability makes them convenient for people who want to eavesdrop, because you only need to point your equipment once. The researchers who did this described their findings in a paper called “Don’t Look Up: There Are Sensitive Internal Links in the Clear on GEO Satellites.”
The team scanned the IP traffic on 39 GEO satellites across 25 distinct longitudes with 411 transponders using consumer-grade equipment. About half of the signals they captured contained clear text IP traffic.
This means there was no encryption at either the link layer or the network layer. This allowed the team to observe internal communications from organizations that rely on these satellites to connect remote critical infrastructure and field operations.
Among the intercepted data were private voice calls, text messages, and call metadata sent through cellular backhaul—the data that travels between cell towers and the central network.
Commercial and retail organizations transmitted inventory records, internal communications, and business data over these satellite links. Banks leaked ATM-related transactions and network management commands. Entertainment and aviation communications were also intercepted, including in-flight entertainment audio and aircraft data.
The researchers also captured industrial control signals for utility infrastructure, including job scheduling and grid monitoring commands. Military (from the US and Mexico) communications were exposed, revealing asset tracking information and operational details such as surveillance data for vessel movements.
The research reveals a pervasive lack of standardized encryption protocols, leaving much of this traffic vulnerable to interception by any technically capable individual with suitable equipment. They concluded that despite the sensitive nature of the data, satellite communication security is often neglected, creating substantial opportunities for eavesdropping, espionage, and potential misuse.
The researchers stated:
“There is a clear mismatch between how satellite customers expect data to be secured and how it is secured in practice; the severity of the vulnerabilities we discovered has certainly revised our own threat models for communications.”
After the scientists reported their findings, T-Mobile took steps to address the issue, but other unnamed providers have yet to patch the vulnerabilities.
This study highlights the importance of making sure your communications are encrypted before they leave your devices. Do not rely solely on providers to keep your data safe. Use secure communication apps like Signal or WhatsApp, choose voice-over-internet (VoIP) providers that encrypt calls and messages, and protect your internet data with a VPN that creates a secure, encrypted tunnel.
We don’t just report on privacy—we offer you the option to use it.
Privacy risks should never spread beyond a headline. Keep your online privacy yours by using Malwarebytes Privacy VPN.