We usually tell our faithful readers to install updates as soon as possible, but this time there’s an exception. Microsoft’s October security update has disabled USB mice and keyboards in the Windows Recovery Environment (WinRE).
WinRE is a special mode built into Windows that helps you fix problems when your system won’t start normally. Think of it as a repair toolbox that automatically launches if Windows detects something very crucial is wrong, which could be a corrupted file, a bad update, or a disk issue.
But recovery mode is not much use when it doesn’t let you use your USB-wired mouse and keyboard.
The security update that broke this functionality is published under the KB5066835 October 2025 security updates as Microsoft revealed:
“After installing the Windows security update released on October 14, 2025 (KB5066835), USB devices, such as keyboards and mice, do not function in the Windows Recovery Environment (WinRE).”
So, to be clear, this isn’t an immediate problem for everyone. As long as your machine behaves normally, it’s not an issue. But if you’re one of the unlucky ones who has to use recovery mode after this update, that’s two problems for the price of one: a broken system and a recovery mode that won’t let you fix it..
Even if you have a Bluetooth mouse lying around, it won’t help. In WinRE the system loads a minimal set of drivers to keep things simple and stable for troubleshooting. Typically, this environment does not support adding or installing new hardware drivers on the fly, including Bluetooth drivers.
Your peripherals will only work if you’re very lucky and have PS/2 connectors (I checked all my Windows machines and only one old desktop has those). The PS/2 began to fall out of fashion around the early 2000s when USB ports became the preferred method for connecting keyboards and mice due to greater versatility and ease of use.
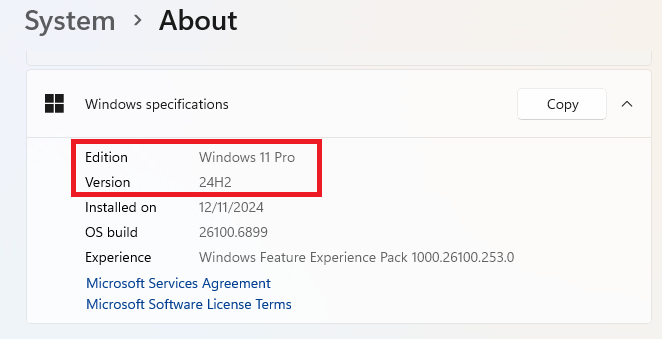
The issue is known to affect both client (Windows 11 24H2 and Windows 11 25H2) and server (Windows Server 2025) platforms.
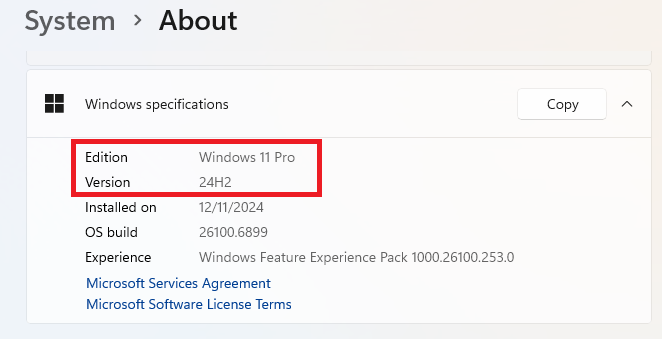
You can find your version by right-clicking on the Windows icon (usually 4 blue squares in the lower left corner) and choosing System. From there scroll down to “Windows specifications.”
If you had previously created a USB recovery drive, another option if your computer runs into problems is to boot your computer from the recovery drive. This will take you directly to WinRE with restored USB functionality.
Tips
If you have a stable system and already installed the update, I would not go as far as to uninstall it, but if you’re worried, you can:
- If Windows is still working normally:
- Go to Start > Settings > Windows Update.
- Click Update history > Uninstall updates.
- From the list, find the update named KB5066835 or one installed around October 14, 2025.
- Select it and click Uninstall. This will remove the problematic update, restoring USB input in WinRE.
- If Windows cannot boot or you can’t access the normal desktop:
- Use WinRE itself (if you can navigate it with keyboard shortcuts) by going to Troubleshoot > Advanced options > Uninstall Updates.
- Choose to uninstall the latest quality update (the offending patch).
Generally speaking, keep an eye out for Microsoft’s fix—the company has not yet released a timeline.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.