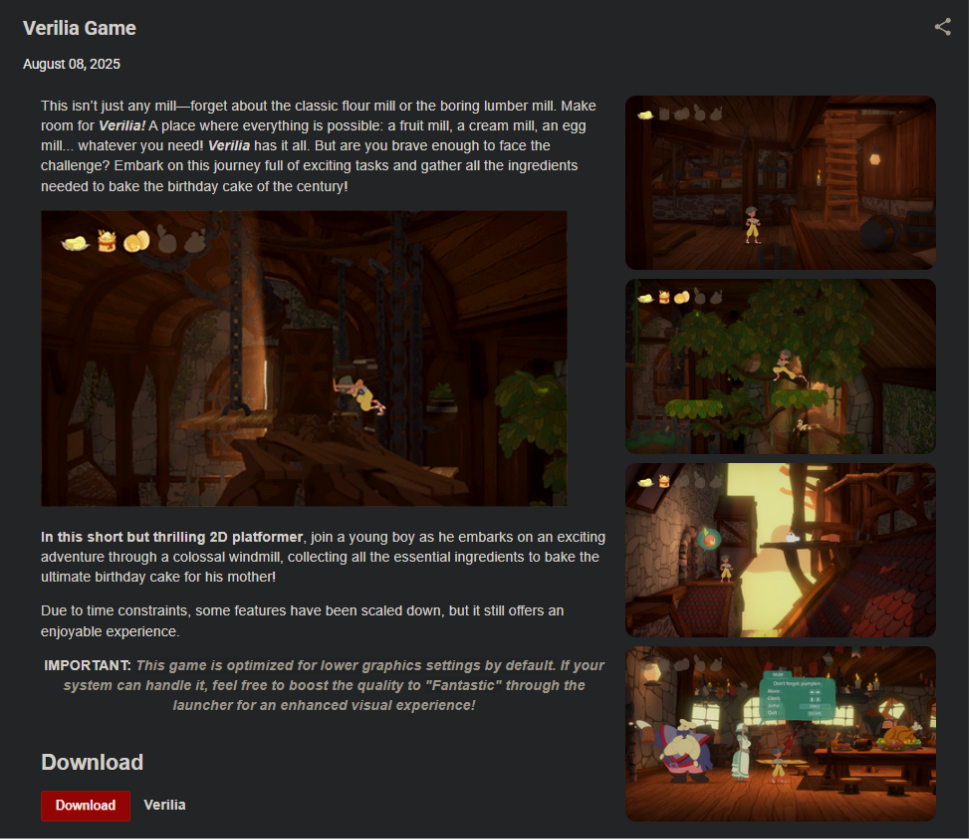
You get a message from a Discord friend. Or maybe an unknown indie developer reaches out to you. “Can you test my game?” they ask.
The webpage they send over a link to looks legit: screenshots, dev blurb, itch.io-style layout, and the download button is right there, waiting to be clicked.
The problem is these lookalike pages don’t give you the real game. Instead they drop a stealthy loader that quietly prepares your PC for follow-up malware.
One lure we’ve seen impersonates the popular 2D platformer Archimoulin (the real game can be found here: nicolasduboc.itch.io/archimoulin).

How they spread it – social engineering 101
This scam nails two things gamers trust: friends and downloads.
- A trusted delivery channel. The lure often arrives in a DM from someone in your friends list—usually because the attacker used a compromised account. People are far more likely to click links from friends.
- Familiar hosting and UI. The impersonators use Blogspot subdomains or cloud links and fake itch-style pages so the site looks legitimate. Sometimes downloads are served via Dropbox or similar service people trust.
- A convincing sign-in page. Some variants present a fake Discord sign-in page first to harvest credentials. This hands the attacker control of your account, which they can use to spread the link to your contacts.
Reddit threads from victims show this pattern again and again: an innocuous “test my game” DM, a convincing page, then account takeover and mass-messaging to the victim’s friends.
What actually happens when you click?
Here’s what the user sees, and what the stealth loader is really doing:
- Double-click the downloaded
Setup Game.exeand… nothing obvious happens. No installer UI, no progress bar. (That’s deliberate – the attacker wants the install to happen without alarming you.)
- The executable spawns PowerShell with a long, encoded command. (Attackers hide commands in encoded strings so the malicious script isn’t obvious at first glance.)
- The command decodes another script and runs it directly in memory. (Running in memory means the malware doesn’t leave a neat file on disk for antivirus to find, so it’s harder to detect.)
- That inner script hides the PowerShell window using a tiny .NET trick, so there’s no black console popping up to make you suspicious. (With no visible window there’s nothing to make you stop and ask what’s running.)
- The code tries to relaunch itself with admin rights (
runAs) and compiles a small helper on the fly usingcsc.exe. (You’ll see temp folders andRES*.tmpfiles while it runs.)
- It unpacks a Node.js runtime and native modules into your user cache (
C:Users<you>.cachepkg...). (The malware is giving itself a toolkit, making it more flexible in what it can do next.)
- The installer even runs
taskkillto force-close major browsers (Chrome, Brave, Firefox, Edge, and Opera). (That stops you from immediately googling what’s happening and then stopping the install.)
- In our sandbox run it didn’t phone home right away; instead it performed checks (net session, registry queries, BIOS/network checks) to confirm it’s on a “real” machine, then waits for the right moment to download the main payload. (Malware often avoids sandboxes, looking for signs it’s on a real user’s computer before unleashing the main payload.)
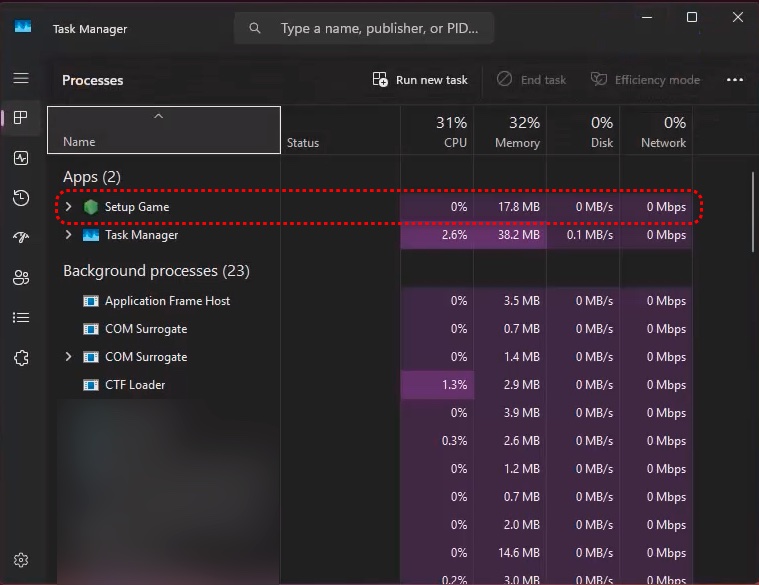
Bottom line: The Setup Game.exe is a stager/loader – quiet on purpose, ready to pull down follow-up malware (backdoors, keyloggers, coinminers, or worse) when conditions match what the attacker wants.
What to watch out for
- Unexpected DM with a download link: If you get a message offering an indie game you didn’t expect, verify it with the sender on another channel first.
- No installer UI but strange behavior after running: If there’s no installer window or progress bar, but your browsers crash or you see temporary compile folders appear, that’s a red flag.
- Unexpected folders appear: Look for new folders you didn’t create, like
C:Users<you>.cachepkg…or%TEMP%xlfvhkx3…especially if you haven’t installed developer tools.
- PowerShell showing
-EncodedCommand: Check running processes logs for signs a hidden script is running.
What to do if you already ran it
Act quickly and use a different, clean device for the first steps.
- From another device, change your passwords (Discord, email, Steam) and enable 2FA.
- Log out all sessions and revoke authorised apps/tokens.
- Disconnect the infected PC and run a full Malwarebytes scan.
- Remove obvious new files/folders (e.g.,
C:Users<you>.cachepkg…,%TEMP%xlfvhkx3…).
- Tell your friends not to click links from your account and report the pages to the host (Blogger/Dropbox) and your platform (Discord/Steam).
- If you see signs of deeper compromise, back up essentials and do a clean reinstall or get professional help.
Final note—indie communities are built on trust
Archimoulin is an indie game; the fake pages are not. Scammers are exploiting the goodwill between players and creators. That’s the worst bit of all: it weaponizes the community itself.
A quick sanity check—to pause, verify the URL, and ask the sender via another app—is all it takes to avoid the hassle of cleaning up a compromised PC (or losing your account and friends). Share this with your clan: one click is all it takes for an attacker to turn a fun, indie moment into a mess.
Indicators of compromise (IOCs)
cakewind[.]blogspot.com
carnagev1[.]blogspot.com
kelarigame[.]blogspot.com
klorigame[.]blogspot.com
meraliagame[.]blogspot.com
ravielchy[.]blogspot.com
ravielchygame[.]blogspot.com
tamunagame[.]blogspot.com
veriliagame[.]blogspot.com
We don’t just report on scams—we help detect them
Cybersecurity risks should never spread beyond a headline. If something looks dodgy to you, check if it’s a scam using Malwarebytes Scam Guard, a feature of our mobile protection products. Submit a screenshot, paste suspicious content, or share a text or phone number, and we’ll tell you if it’s a scam or legit. Download Malwarebytes Mobile Security for iOS or Android and try it today!